The coronavirus crisis has massively accelerated the digital revolution. However, in many cases, IT security is not keeping up. By now, many employees have been working from home for more than six months. At the beginning of the pandemic, companies focused on functionality. Understandably, business continuity was the top priority at first. Now, however, those in charge must put greater emphasis on IT security and comprehensive measures must be taken to avert cyber attacks.
G DATA threat analysis: Further doubling of cyber attacks in Q3
Attackers are still taking advantage of the coronavirus pandemic to attack businesses and home users
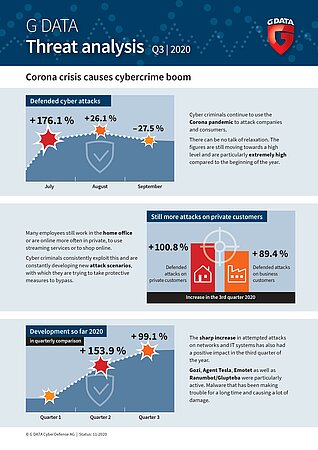
In the third quarter of 2020, cyber defence specialists from Bochum had to fend off almost twice as many cyber attacks as in the second quarter of the year. The attackers are using large-scale campaigns to attack both private computers and company networks. Intense activity has been observed in particular among malware programs such as Emotet, Agent Tesla, Gozi and RanumBot. The main contributors the boom in cybercrime are people’s insecurity during the coronavirus crisis as well as the high number of employees continuing to work from home.

Cyber crime - a seasonal business
Cyber criminals were particularly active in July 2020. The number of attempted attacks increased by 176.1 percent compared to June - the highest increase within a four-week timeframe during the current year. After the sharp increase in July, the situation calmed down somewhat in August and September. Security analysts in Bochum have recently recorded a decline in cyber attacks. From August to September, the number dropped by 27.5 percent.
Looking at the big picture however, there is no question of a let-up - the figures remain at a high level, and are very high compared to the beginning of the year especially. The decrease in attacks demonstrates that cyber crime is undergoing seasonal fluctuation. The number of attempted attacks traditionally increases at the beginning of the summer holiday season. For example, criminals send out mass emails containing supposedly cheap or fake holiday offers. This year, sending false warnings regarding travel and coronavirus was another scam used by the perpetrators. Another reason for the decline is that attackers repeatedly make adjustments to their malware or IT infrastructure before launching the next wave of attacks. The aim of this is to improve efficiency in order to increase profits.
Long-known malware
In total, analysts at G DATA identified 200 active malware families in the third quarter. Gozi, Agent Tesla, Emotet and Ranumbot/Glupteba were particularly active. These are malware strains that have been making trouble and causing a great deal of damage for some time.
Gozi, for example, has been around since 2006. This malware usually penetrates victims' systems via phishing emails and has screen capture and keylogging functions. Gozi uses its functionality to glean login data stored in browsers and email software.
After a break this spring, Emotet, the all-purpose weapon of cyber criminals, has picked up speed again. The malware is now very complex. Its original function - the manipulation of online banking transactions - is now a thing of the past. Emotet has moved on to other areas for this purpose, from tapping into email contacts and creating detailed communication profiles of attack victims, to acting as a door opener for other malware.
Agent Tesla has been active for more than six years. This is a sophisticated keylogger and information stealer that records keystrokes, reads data, generates screenshots and intercepts access data. Attackers are now combining these attacks with current social engineering methods and including references to COVID-19 in phishing emails, so they are still causing a great deal of damage.
RanumBot deactivates all security services and the Windows firewall on an infected system, thus opening the door for further malware such as the Trojan Glupteba. In addition, the malware changes the default settings in the Windows registry so it is activated automatically each time Windows is restarted.

The IT security situation remains critical. Cyber criminals are constantly developing new attack scenarios, which they also use to try to circumvent protective measures. It is no longer enough to rely solely on technological protective measures. Attacks through social engineering can be particularly hard to prevent through technical means. Companies must therefore make sure their employees can detect cyber attacks at an early stage. Security awareness training and phishing simulations are a good way to approach and improve IT security in a holistic way.