Going to the restroom with the laptop during a long meeting - and not noticing that the camera is still on. Experiencing how the boss can no longer switch off his amusing avatar and has to lead the online conference as a potato. A lot can go wrong when working from home - in terms of collaboration, but also in terms of IT security. Here are the most important tips to ensure that everything runs smoothly. How does the cooperation with colleagues work? What are the dangers for IT security in the home office? How can employees protect themselves? And: How do IT administrators set up a secure home office?
of the companies have had IT security incidents attributable to home office work since the start of the Corona pandemic.
(Source: Wirtschaftsschutz 2021, bitkom)
professionals in Germany now works from a home office.
(Source: Hans-Böckler-Stiftung, 2021)
8 simple tips for a successful home office routine
- Distraction-free environment
If possible, provide an undisturbed environment. Your partner, children or pets should not distract you - all the better if you have your own study. If you are working at home with your partner, make arrangements with him/her as to who will look after the children and at what times, so that the other person can work in a concentrated manner. - "Anyone who wears sweatpants has lost control of their life" - Karl Lagerfeld.
It's not quite that bad, of course. But if you drag yourself out of bed minutes before the first meeting and do wear your sweatpants, it can have a negative impact. The problem is not casual dress, but that at home the boundaries between work and private life quickly become blurred. Therefore, create new routines for yourself: Start every morning with a cup of tea and move away from the workplace or your study at the end of the working day. Start the end of the day with a ritual, such as putting on casual clothes and cooking something delicious. - Plan your day and set priorities
As nice as flexible working is, when you work undisturbed in your own home, it's easy to forget the time and sit on your tasks until late in the evening. Therefore, briefly coordinate with your closest colleagues in the morning and make a list of what is due for the day and what is most important. When these tasks are done: PC off, relaxation on. - Increase well-being
Set up a pleasant workplace with your favourite furniture and decorative elements. Ventilate regularly, relax your eyes by looking out of the window and drink plenty of water. Sitting for long periods of time is bound to cause a tense neck and back pain. Dynamic sitting and 5-minute breaks with stretching exercises using online videos can work wonders. After lunch, take a short walk around the block during your lunch break for energy and sunshine. Set blockers for breaks to really stick to them. - A picture is worth 1,000 words - use video chats
In text chats, discussions go back and forth too often and information is still missing. A quick video call is therefore many times more effective. Advantage: Seeing the facial expressions of our colleagues prevents misunderstandings. In regular video meetings, an agenda and timetable help to keep the thread and the common goal in sight. Don't worry if your child appears in the video: Everyone will understand, because we are all human. - Regular exchange strengthens togetherness
And promotes the flow of information. Teams should consider setting up daily calls. The advantage is that you are guaranteed to stay up to date and problems as well as experiences can be discussed easily. Also open a "kitchen channel" where colleagues can meet casually while cooking or having a coffee on the balcony.
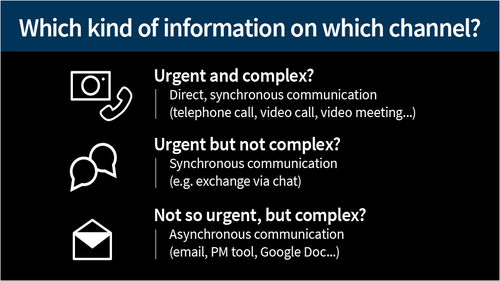
- Communicate information in a targeted way
Constantly and unfilteredly distributing information in the project chat leads to the team often being disturbed. In the worst case, questions remain unanswered, which are then discussed at length and without results. As long as you can't really contribute relevant news in team chats, you should reduce your participation to the essentials. - Set rules for communication
A colleague writes something to the team via channel A, someone replies on channel B and yet another gets back to you via channel C: if communication takes place on different platforms, it quickly becomes exhausting and important information gets lost. It is best to agree on common rules about which communication channels are used for what.
What cyber dangers lurk in the home office?

The slumbering enemy in the network
The number of cyber attacks was up by about 30 percent in March compared to February 2020, according to a threat analysis by G DATA CyberDefense. Many companies had to send their employees to their home desks to work virtually overnight due to the Corona crisis. However, home office "emergency solutions" set up under high time pressure often harbour numerous security gaps.
The danger posed by backdoors is particularly high at the moment, because an attacker can move around the company's network and collect information relatively undisturbed for months, even beyond the acute crisis - and attract little or no attention. Criminals can "sit out" the current crisis in the IT infrastructure - and then strike when something like normality returns.
People as targets
In addition to direct attacks on IT networks, criminals shamelessly exploit people's fear and uncertainty about Corona:
- Dangerous email attachments:
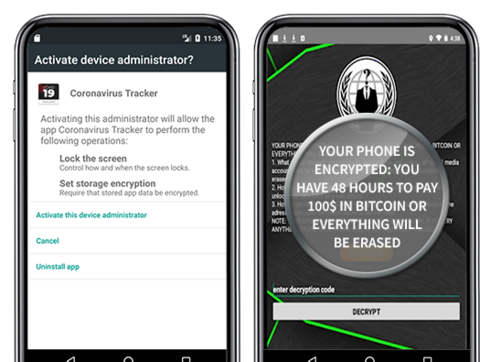
Who would ignore a supposed mail from a boss or IT colleague containing an attachment called "COVID-19-New_Home_Office_Regulation_From_June.doc"? Or announcing seemingly important regulations from the WHO or a health authority? Criminals are currently sending out more and more deceptively genuine e-mails with dangerous attachments. As soon as someone opens the attachment, spy software is installed on the PC. Or the device is completely encrypted by ransomware. In order to decrypt it again, the criminals demand high sums of money from their victims. - Malicious links:
Criminals use social media and emails to spread fake news about supposedly ready-made vaccines, special offers on protective masks or misleading advice. Users are supposed to click on a link. This, however, leads to a malicious website that loads malware onto the PC unnoticed. - Data theft with phishing:
In fraudulent messages via e-mail or social media, criminals ask users to disclose confidential data, such as passwords, access data or credit card numbers. To do this, they are supposed to click on a link and enter the data there. However, these links lead to fake websites where the data is tapped. In this way, criminals can quickly gain access to the company, for example to confidential documents of the employer.
What helps in these cases? Train your employees in secure behaviour: In the practice-oriented e-learning trainings from G DATA, employees learn how to recognise and ward off phishing and learn everything else important about IT security and data protection.
Examples:
IT security in the home office: What should employees be aware of?
- Do not connect private flashdrives
Even if you are sitting at your desk in your own home: You are connected to your employer's network. Therefore, here as well as in the office, do not connect any flashdrives or external hard drives of you or your friends to the company-owned PC. This way you reduce the risk of your computer being infected with malware. - Beware of e-mails
Phishing e-mails arrive in your inbox even when you are working at home. Many are currently being sent especially in relation to the corona virus. Therefore, pay special attention to e-mails to see if they could be phishing e-mails with a link to a malicious website or a dangerous attachment. You should also be vigilant about invitations to new communication tools from your employer - they could be forged by criminals. - Use passwords and encryption
Employees should make sure that not only their PC or laptop is protected with a secure password, but also that the hard drive and any external storage media are encrypted by the employer. If necessary, ask your IT department to help set this up. You can find the most important tips for a secure password in our advice article. - Secure your private Wi-Fi connection
If you haven't done it before, you should do it at the latest when you work at home in your private WLAN: Secure your Wi-Fi connection so that intruders cannot gain access. The WLAN should be encrypted with WPA2 and use a MAC filter. Also set a secure network password. An alternative would be to create a second guest WLAN. Advantage: This way you have a network separation between the private network and the connection with your company.
- Save your work on the company network
It is best to save your documents and work results on the data carriers in your employer's network and not locally on your PC. That way, your data is safe, even if there's a problem with your PC. - Do not transfer large data
If you can avoid it, do not transfer large amounts of data to or from the company network. This keeps the load on the company VPN to a bearable level and prevents the connection from being slowed down for other employees. - Protect paper documents - including paper waste
If you work with paper documents containing confidential or personal data, you should keep them locked away. Official paper documents do not belong in normal household waste. Shred them in a shredder or take them with you the next time you go to the office and dispose of them properly there. - No eavesdropping on phone calls
A delicate phone call about the latest quarterly figures? Go to an undisturbed area for all professional phone calls so that other people in the building do not hear anything about the content of your phone calls. - Delete call contacts and do not transfer numbers
If you use your private telephone for business, regularly delete automatically saved call contacts. Set your telephone so that your private number is not transmitted when you make a call so that customers or business partners do not receive your private number. - Beware of "home office pictures"
If you participate in what is happening on social media and post pictures of the job at home: make sure that no personal information or employer data is visible in photos, such as emails, open documents, etc. - Do not leave work unattended
When you leave your workplace or study after work is done or even for a short time: Always activate the screensaver with password protection so that no one can access the content, including family members. This way you ensure that no one accidentally sends e-mails or deletes important results of your job. - Screen - top secret
It's best to have a home office workstation in its own room or corner. Choose the place of your desk so that others cannot see the screen - not even through a window.
Set up a secure home office: Here's how
Checklist for IT departments
- Provide company-owned devices
Provide your employees with company-owned devices, such as laptops. If no laptops are available, give them stationary workstation computers to take home. However, this should be an absolute emergency solution and requires adequate security. - Set up a VPN to connect to the company network
With a VPN, it makes no difference whether an employee does their job in the office or at their desk at home. VPN is a basic prerequisite for securing communication, because you establish a secure tunnel. With a VPN connection, employees send and receive all information via a secure connection. Find out more about secure solutions. - Activate multi-factor login for the VPN
When an employee connects to the VPN, he or she should not only enter a password for security reasons, but also carry out another authentication via a second channel. This can consist, for example, of a hardware token such as a USB stick or, even better, an OTP app ("One-Time-Password"), which generates a unique password for each login that is only valid for that particular login. This ensures unique verification. - Seek advice from IT experts
A single gap is enough to open the door to the employer's network for cyber criminals. To prevent such incidents, it is advisable to have your own remote infrastructure scrutinised by IT security experts. - Activate hard disk encryption
Activate hard disk encryption on home office devices. This way, even the loss of a device does not lead to a data protection problem. - Define clear requirements for access
VPN access is of no use if your colleagues cannot access files and applications within the network. But also check which VPN accesses and authorisations exist at all and which can be restricted so as not to open the gate unnecessarily wide. - Set up VoIP telephony or call diversions
Configure VoIP telephony (if available) so that it works remotely. Alternatively, set up the internal telephone system so that calls are diverted to the private telephone line or the work mobile phone. - Secure tools for chats and video conferences
E-mails to distribution lists several metres long bring one thing above all: chaos. Chat tools are therefore indispensable. The tool should use end-to-end encryption. Choose a tool that suits your needs: Can it also hold video conferences for digital meetings? Does it need to allow for the secure exchange of files? Should it be possible to share the screen with colleagues? - Installing updates
Of course, it is now more important than ever to install updates immediately. Make your employees aware of this issue as well. - Good monitoring
Use data sources sensibly and carry out monitoring. The best logging is useless if you do not use the data and do not visualise it sufficiently. In the end, entire departments may not be able to work properly because no one has noticed that the firewalls are in the red zone. Or you may not notice a security incident, for example if someone breaks into the company network. - Build up redundancies
High availability is not a luxury, but a necessity for survival. If only one firewall is in use, a single component failure is enough to bring the entire operation to a standstill. That's why it's important to build up redundancies. It is better if only 20 or 30 colleagues are temporarily unable to work instead of the entire staff.

Get employees on board (securely)
- Train employees in IT security:
Cybercriminals often target employees directly. The best protection is for employers to make their employees aware of security-related issues. How do they protect sensitive data at home from unauthorised access? Why do they need to schedule time for regular backups and updates? The best way to do this is through short e-learning trainings. - Communicate contact persons:
Provide your employees with one or more contact persons from the IT department, including contact details, from whom they can get answers to their questions. Employees should also contact these people if paper documents or data carriers have been lost. - Guides and instructions:
Communicate clear and binding rules on IT security in guides. Also give employees instructions on common questions, such as how to set up certain tools. Tip: Write them as clearly and in small steps as possible. And: A picture is often worth a thousand words. - The problem of the door lock de-icer being inside you car:
When transitioning to the home office, it does employees no good if they first have to connect to the VPN in order to read the VPN setup instructions. Therefore, especially in the beginning, make sure that employees can access help and instructions, for example through telephone IT support or a public chat environment that is accessible from the internet but sufficiently secured (https and authentication). - Announce tool invitations:
Attackers send phishing emails with tool invitations in which workers are supposed to click on a link to set up the tool. The fake website then grabs company credentials. The most important prerequisite for protection: clearly communicate to your employees which tools will be used and which invitations they will receive for them by email.